How Zcash Shielded Pools Work in Zaunchpad
Zaunchpad uses Zcash shielded pools to protect privacy for token launch participants. This guide explains how shielded pools work and how deposits from NEAR Intents flow into them.
1. What are Zcash Shielded Pools?
Zcash shielded pools are private transaction systems that allow transfers without revealing:
- Sender Identity: Who sent the transaction
- Receiver Identity: Who received the transaction
- Transaction Amount: How much was transferred
- Transaction History: Previous transactions
Key Concepts
- Shielded Transactions: Completely private transactions within the pool
- Anonymity Set: The group of all users transacting in the pool
- Zero-Knowledge Proofs (zk-SNARKs): Cryptographic proofs that allow verification without revealing data
- Unified Shielded Pool: Unified mechanism that severs links between capital source and destination
2. How Shielded Pools Work
Shielded pools use zk-SNARKs to:
- Prove Validity: Show transaction is valid without revealing information
- Maintain Privacy: Keep all transaction data hidden
- Enable Verification: Allow validators to verify without knowing details
- Break Links: Sever all on-chain connections between input and output
Transaction Flow
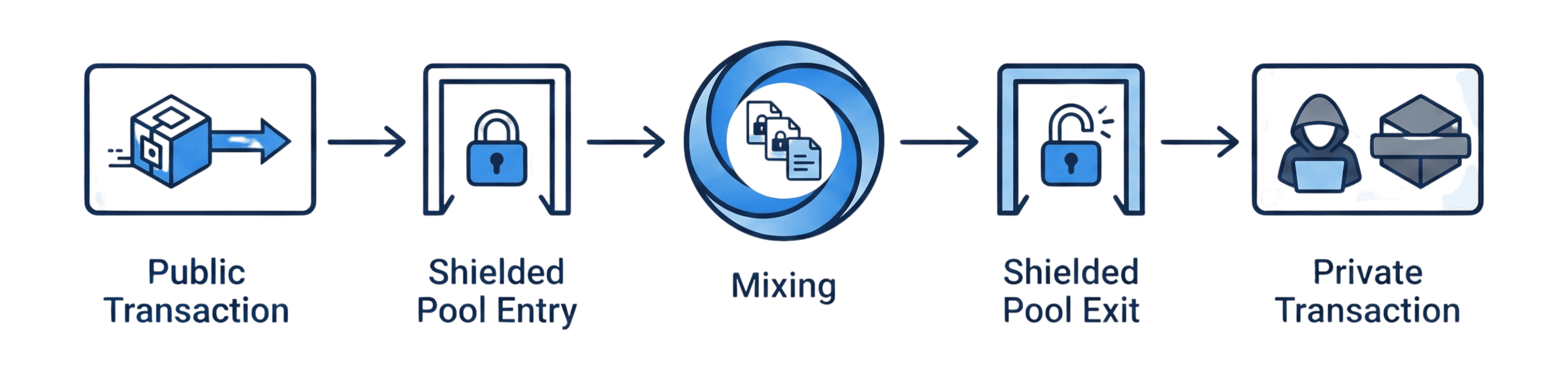
Process
- Entry: Funds enter the pool
- Mixing: Mixed with other transactions
- Anonymity: Identity blends into the user set
- Exit: Exits pool as private transaction, source not revealed
Cryptographic Guarantees
- Soundness: Invalid transactions cannot be proven
- Completeness: Valid transactions can always be proven
- Zero-Knowledge: Proofs don’t reveal information
- Privacy: All links are hidden
3. How NEAR Intents Deposits Flow into Shielded Pools
Complete Flow
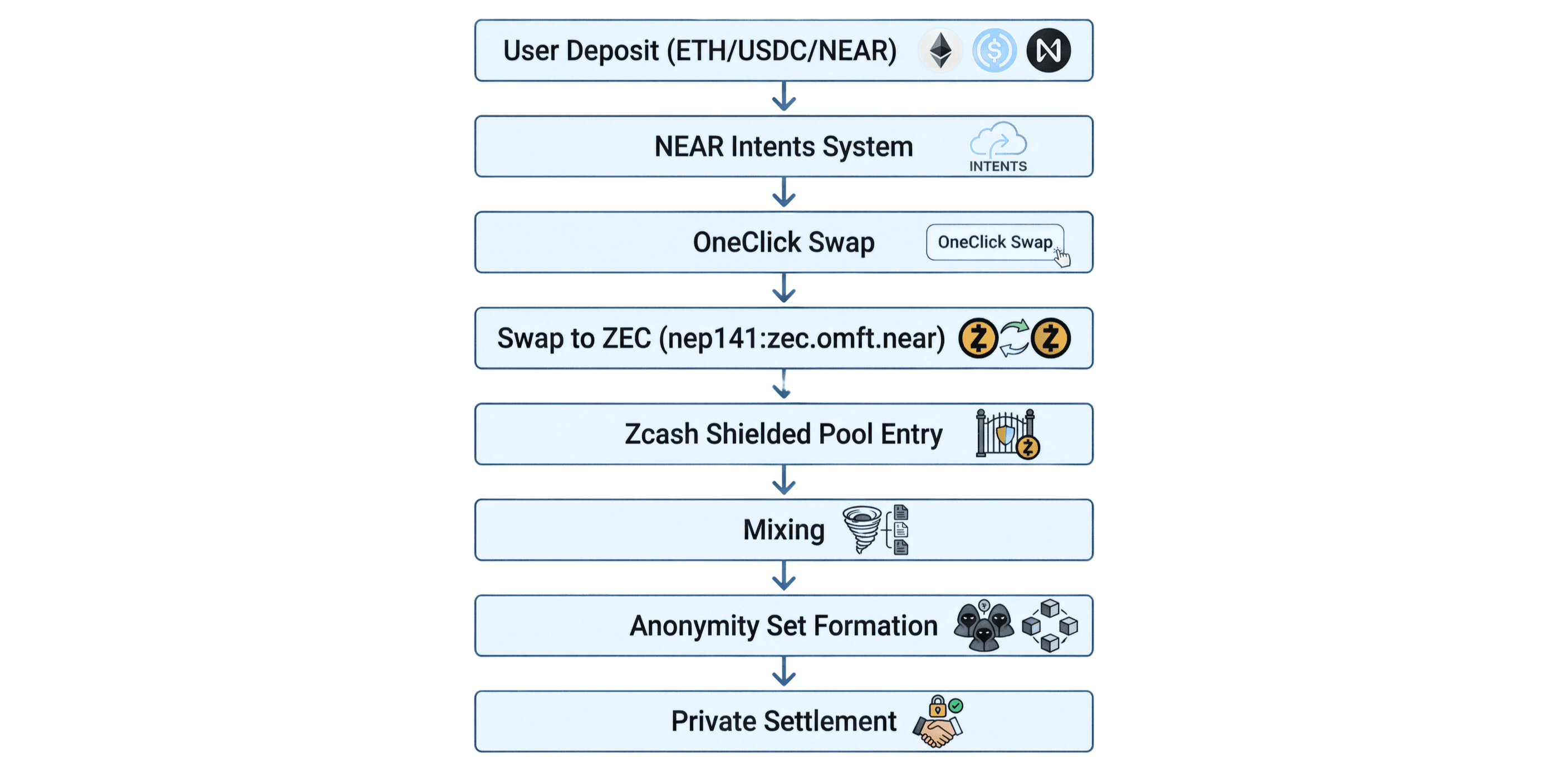
Detailed Steps
Step 1: Deposit via NEAR Intents
- User deposits ETH/USDC/NEAR (or supported tokens)
- Creates intent: “Swap X tokens to ZEC”
Step 2: Automatic Swap
- NEAR Intents uses OneClick Swap to convert to ZEC on NEAR (nep141)
Step 3: Entry into Shielded Pool
- ZEC is sent to Unified Shielded Pool
- Source identity is completely severed from the shielded transaction
Step 4: Mixing
- Transaction mixes with all ZEC in the pool
- Hides amounts, timing, and source
Step 5: Anonymity Set Formation
- Larger pool → stronger anonymity
Step 6: Private Settlement
- ZEC is settled in the pool
- Ready for TEE verification process
4. How Zaunchpad Uses Shielded Pools
Process for Launch Participants
- You deposit via NEAR Intents
- System automatically swaps to ZEC
- ZEC enters shielded pool
- Mixing happens automatically
- You’re added to anonymity set
- Phala TEE verifies and generates ZK proof
- You claim tokens without revealing identity
Benefits
- Source Privacy: Original token source is hidden
- Address Privacy: Your address is hidden
- Amount Privacy: Transaction amount is hidden
- No On-Chain Link: No connection between deposit and claim
- Mathematical Security: Privacy guaranteed by cryptography and TEE
5. Anonymity Set
Definition
Anonymity set = the number of users whose transaction yours could be.
Examples
- Size = 1: No anonymity
- Size = 10: 10% chance of correct guess
- Size = 100: 1% chance
- Size = 1000: 0.1% chance
In Shielded Pools
More participants → stronger privacy.
6. Privacy Guarantees
What is Protected
✅ Identity: Who you are remains hidden ✅ Amount: Transaction amount is private ✅ Timing: When you participated is obscured ✅ Source Token: Original deposit token is hidden ✅ Deposit-Claim Link: No connection between deposit and claim
What is Not Protected
❌ Information You Reveal: Data you share publicly ❌ Timing Attacks: If pool is small ❌ Off-Chain Metadata: External information
7. TEE (Phala Trusted Execution Environment)
TEE ensures:
- Private Execution: Transaction data runs only in private environment
- No Visibility: No validator can see contents
- Attestation: Cryptographic proof of correct execution
- Secure Processing: Swaps and ZK proofs generated in secure enclave
- Tamper-Proof: Cannot be modified or interfered with
8. How to Use Shielded Pools
For Users
- Deposit via NEAR Intents
- System automatically enters pool
- Wait for mixing
- Claim using ZK proof
For Creators
- Enable Privacy: Privacy is enabled by default
- Monitor Pool: Track pool metrics
- Respect Anonymity: Don’t reveal user identities
9. Best Practices
Do’s
✅ Wait for Mixing: Allow time for transactions to mix ✅ Check Anonymity Set: Verify sufficient size before participating ✅ Keep Private: Don’t share addresses publicly ✅ Trust the System: Privacy is mathematically guaranteed
Don’ts
❌ Don’t Reveal Timing: Don’t announce when you’ll participate ❌ Don’t Use Small Pools: Avoid pools with few participants ❌ Don’t Self-Reveal: Don’t reveal your identity publicly